We’re working on an ASP.Net project that uses Identity to handle user authorization and had an interesting issue when creating temporary email confirmation tokens.
The tokens are generated via the Use-Manager’s function “GenerateEmailConfirmationTokenAsync”. Then we add that token to a link which is emailed to the user.
Periodically, these tokens were coming back as being invalid and a search on the issue came up with some interesting reasons.
public class ApplicationUserManager : UserManager<User>
{
public ApplicationUserManager(IUserStore<User> store)
: base(store)
{
}
public static ApplicationUserManager Create(IdentityFactoryOptions<ApplicationUserManager> options, IOwinContext context)
{
var manager = new ApplicationUserManager(new UserStore<User>(context.Get<RjwContext>()));
// Configure validation logic for usernames
manager.UserValidator = new UserValidator<User>(manager)
{
AllowOnlyAlphanumericUserNames = false,
RequireUniqueEmail = true
};
manager.PasswordValidator = new PasswordValidator
{
RequiredLength = 6,
};
var dataProtectionProvider = options.DataProtectionProvider;
if (dataProtectionProvider != null)
{
manager.UserTokenProvider =
new DataProtectorTokenProvider<User>(dataProtectionProvider.Create("ASP.NET Identity"))
{
TokenLifespan = TimeSpan.FromDays(14)
};
}
return manager;
}
}
In IIS settings for a specific site, there’s a button labeled “Machine Key” and if you double-click on this you’ll see the following screen:
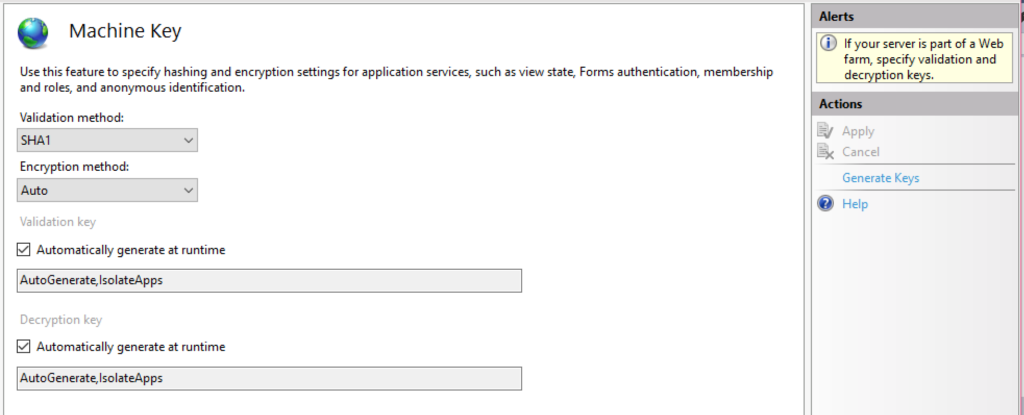
Uncheck both checkboxes and click into each text-box and then click on “Generate Keys” on the right side. This will simply force the machine keys to be the same every time this site is used (or IIS gets restarted, etc).
As a side, when the user sets this configuration, IIS adds a machine key element in the site’s web.config file. To guarantee that the site always uses that machine key, we copied that section into web.config of the project in our Github repository.